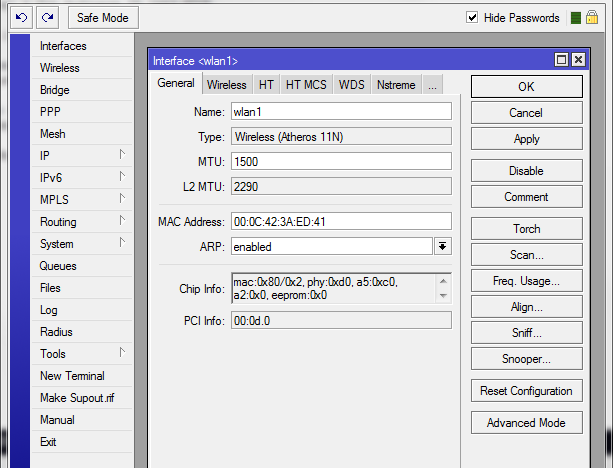
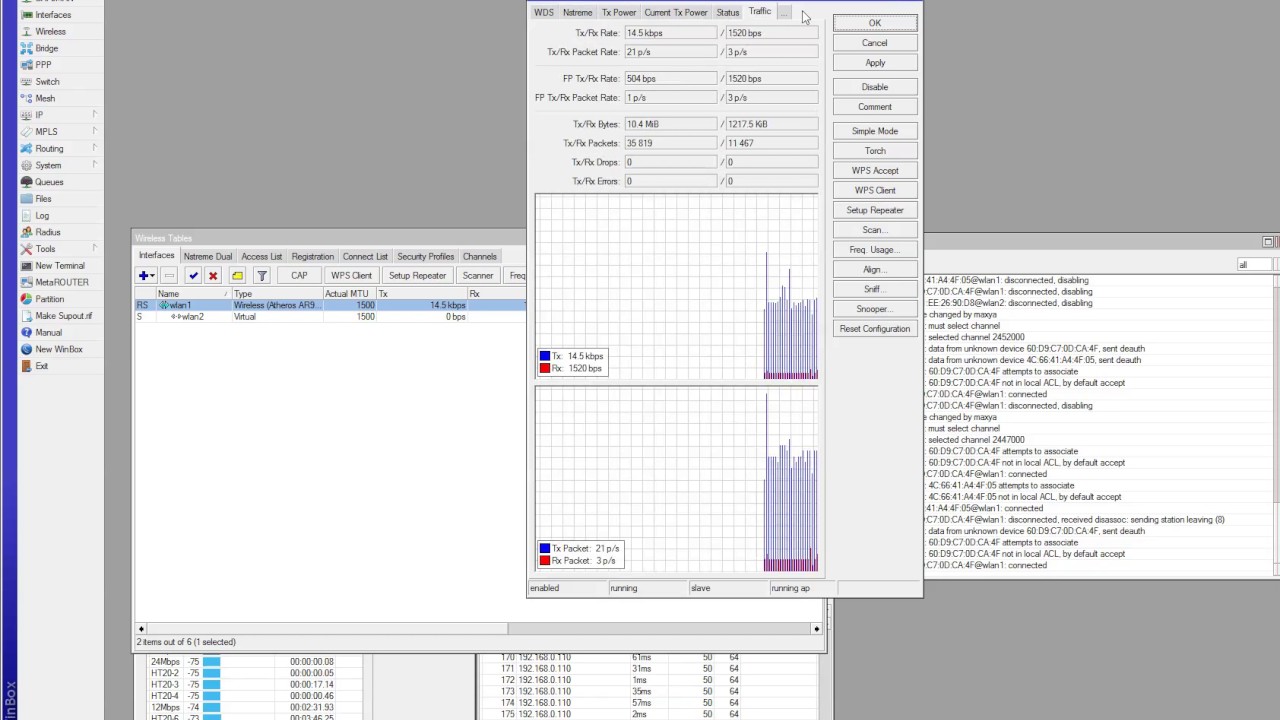
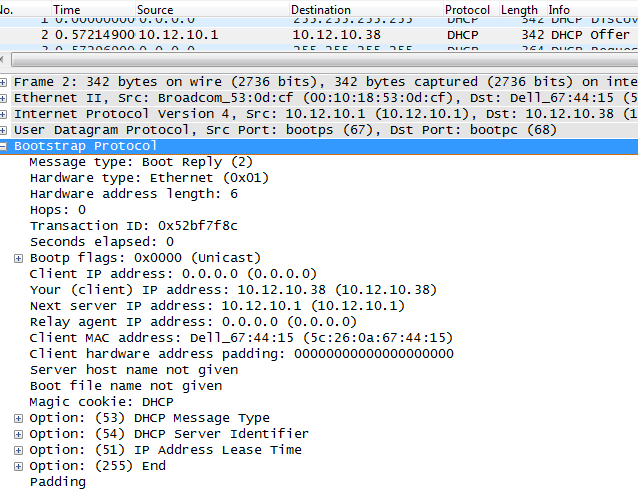
MikroTik Switching With LABS - Master Switching On MikroTik - All Topics in The MTCSWE Certification Exam Are Covered. | PDF | Network Switch | Computer Network
![Mikrotik - Second Part [Interface and Configurations] by : Mohamed Ahmed. « Null Byte :: WonderHowTo Mikrotik - Second Part [Interface and Configurations] by : Mohamed Ahmed. « Null Byte :: WonderHowTo](https://img.wonderhowto.com/img/84/96/63640748179483/0/mikrotik-second-part-interface-and-configurations-by-mohamed-ahmed.w1456.jpg)
Mikrotik - Second Part [Interface and Configurations] by : Mohamed Ahmed. « Null Byte :: WonderHowTo
![Mikrotik - Second Part [Interface and Configurations] by : Mohamed Ahmed. « Null Byte :: WonderHowTo Mikrotik - Second Part [Interface and Configurations] by : Mohamed Ahmed. « Null Byte :: WonderHowTo](https://img.wonderhowto.com/img/38/80/63640747711671/0/mikrotik-second-part-interface-and-configurations-by-mohamed-ahmed.w1456.jpg)
Mikrotik - Second Part [Interface and Configurations] by : Mohamed Ahmed. « Null Byte :: WonderHowTo
![Mikrotik - Part Three [Breaking Chains for the Administrator] by: Mohamed Ahmed « Null Byte :: WonderHowTo Mikrotik - Part Three [Breaking Chains for the Administrator] by: Mohamed Ahmed « Null Byte :: WonderHowTo](https://img.wonderhowto.com/img/56/30/63640870428602/0/mikrotik-part-three-breaking-chains-for-administrator-by-mohamed-ahmed.w1456.jpg)
Mikrotik - Part Three [Breaking Chains for the Administrator] by: Mohamed Ahmed « Null Byte :: WonderHowTo
![Mikrotik - Part Three [Breaking Chains for the Administrator] by: Mohamed Ahmed « Null Byte :: WonderHowTo Mikrotik - Part Three [Breaking Chains for the Administrator] by: Mohamed Ahmed « Null Byte :: WonderHowTo](https://img.wonderhowto.com/img/66/80/63640869840968/0/mikrotik-part-three-breaking-chains-for-administrator-by-mohamed-ahmed.w1456.jpg)
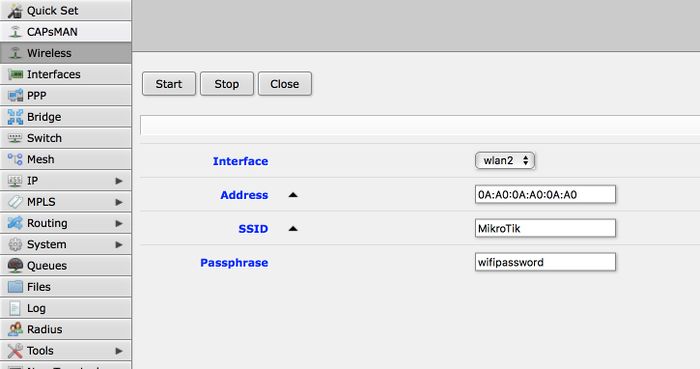




![Mikrotik - Part Four [UnderTaker - QoS]by : Mohamed Ahmed. « Null Byte :: WonderHowTo Mikrotik - Part Four [UnderTaker - QoS]by : Mohamed Ahmed. « Null Byte :: WonderHowTo](https://img.wonderhowto.com/img/29/03/63640872615206/0/mikrotik-part-four-undertaker-qos-by-mohamed-ahmed.w1456.jpg)